Whether you realize it or not, cyber security is one of the greatest risks facing small and medium businesses today. Not only are digital crooks and cyber fiends better equipped than ever before, but businesses are also using an unprecedented level of web-connected technologies; all of which are vulnerable to attack.
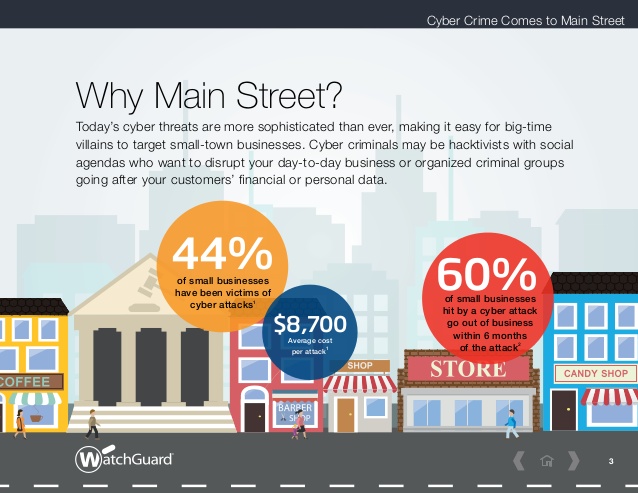
To compound the threat even further, SMBs often lack the same resources and robust security measures implemented by large corporations, which is why hackers are targeting small businesses. In fact, it’s estimated that 43 percent of cyber attacks are aimed specifically at SMBs.
While small businesses are regularly victims of ‘spray and pray’ malware attacks and phishing scams, organizations can reasonably bounce back with little damage. But what about an all-out onslaught? What does a worst-case scenario look like?
The Perfect Storm
It’s Monday morning. Your employees are enjoying a casual start to the week by checking their emails, sipping their coffees and sharing small talk about their weekends.
But around 10:30 a.m. someone notices that your website isn’t working. Actually, none of your sites or services are working. Someone pings IT, who assures them professionals are working on the issue. By 11:45 a.m., everything is back up and running. No problem!
But that’s not exactly true. IT detected a large number of phony web requests made during the hour and a quarter downtime. An obvious sign of a distributed denial-of-service or “DDoS” attack. Things are better now, but your IT team considers various defense strategies just in case your site is hit by another attack.
The attack, although short-lived, did have a noticeable effect on your daily revenue. Depending on the size of your business, the cost of a DDoS attack can range from as little as $1 to more than $100,000 per minute of downtime. Thankfully, the onslaught came just before peak hours, so you lost a few hundred dollars.
But the DDoS attack wasn’t the primary goal of this hacker. Oh no, it was just a smoke screen to upload malware into your network. As Monday ends, the cybercriminal has weaseled their way into your devices, ready for the next phase of the attack.
The Revelation
Fast forward three months. You’ve completely forgotten about the DDoS attack and you suspect it was a one-time fluke. An experiment by an aspiring script kiddie, perhaps.
You see an incoming message from your customer service department. It mentions that many of your users are complaining about spam emails, some of which are being sent to addresses only used for your service! What’s going on here?
Your IT department does a little investigating and discovers that a trove of customer information available for sale on the digital black market, also known as the dark web!
Apparently, one of your employees stored valuable and unencrypted customer data including names, addresses, emails, payment information and sign-in credentials. Now that data is up for grabs.
Before you know it, the office is in crisis mode. Teams mobilize to alert customers of the data breach, contain bad PR, quarantine affected customer accounts – there’s just too much to do!
Regrettably, the hacker’s tendrils are still in your network and they are monitoring communications being sent between employees. They suspect there is little else to pilfer from your fledgling company, so they decide to give you one last squeeze and launch a ransomware attack – crippling your operation from the inside until a lump sum is paid.
Insult to Injury
Flash forward six months. Your business is locking its doors for good. It just took too much to revitalize your company’s image after the hack, not to mention the financial losses due to the class-action lawsuit. It’s all over.
But hey, you aren’t alone. Turns out that 60 percent of small business go out of business in six months after a cyber-attack.
Don’t let this happen to you! Protect your company by:
- Investing in data breach coverage or cyber security insurance policy to cover the cost of an attack.
- Developing a crisis response plan before disaster strikes.
- Employing a DDoS mitigation service that redirects or blocks malicious traffic.
- Educating your employees about the risk of hacking and cyber crime.
- Installing antivirus and malware protection services.
Follow these tips to keep your business healthy and strong!



